Ever heard that moderation is a "propaganda word" for censorship?
Many praise Telegram’s encrypted chats and open-source framework; its lack of moderation has made it a playground for cybercriminals. Telegram dark web channels mimic underground marketplaces, supporting the distribution of stolen credentials, malware, hacking tools, and more.
Let’s explore the top dark web Telegram channels, their threats, and why protecting your digital footprint is critical, even if you never intentionally access the dark web.
How Dark Web Channels Operate on Telegram
Telegram’s built-in privacy features, such as username-based communication, large group capacities, and optional encryption allow threat actors to operate with little oversight.
Dark web channels often are:
- Marketplaces for stolen credentials
- Repositories for leaked data
- Coordination hubs for DDoS attacks and malware distribution
- Spaces for hacktivist propaganda and recruiting
Unlike traditional dark web platforms accessible via Tor, Telegram lowers the entry barrier, making these operations accessible with just a link.
10 Telegram Channels and Groups That Can Exploit Your Private Data
Many dark web activities have migrated to Telegram due to its minimal content moderation, high group size limits, and optional encryption features. Cybercriminals are using the platform to distribute stolen credentials, financial data, and hacking tools in organized, semi-public channels.
These are 10 dark Telegram groups and forums you must avoid if you value your digital privacy and personal security.
- Moon Cloud – Data Dump Distribution Hub

Moon Cloud is widely known in underground Telegram circles for offering stolen credentials, including usernames, emails, passwords, and IP addresses. This channel operates on a freemium model, where basic leaks are free and more sensitive databases are sold.
It’s a hotspot for cybercriminals targeting account takeovers, credential stuffing attacks, and identity theft. Data posted here is often sourced from malware logs or breached platforms and then redistributed in bulk.
Why it’s dangerous: Even if you’re not an active Telegram user, if your credentials have ever been leaked in a data breach, they could appear here.
- NoName057(16) – Pro-Russian DDoS Coordination Channel
This Telegram group is operated by a pro-Russian hacktivist collective specializing in distributed denial-of-service (DDoS) attacks against government and infrastructure targets. Their operations often include digital propaganda, recruitment drives, and tools for volunteer-led cyberattacks.
NoName057(16) coordinates campaigns by sharing target IPs and DDoS tools, some of which are embedded with malware that can compromise the attacker’s system, too.
Risk Involved: Even browsing their tools or joining out of curiosity may expose your device to tracking, surveillance, or infection.
- RipperSec – Politically Driven Cyber Sabotage

RipperSec is a politically motivated hacktivist group that targets Israeli digital infrastructure and its allies. The channel often features announcements of recent attacks, proof-of-concept vulnerabilities, and defaced websites.
They also share tools that can be repurposed for other attacks, making this a breeding ground for freelance cybercriminals who want to launch politically charged or freelance operations.
Threat level: High. RipperSec’s campaigns often lead to data exposure and system compromise, particularly for people located in target regions.
- Observer Cloud – Aggregator of Breached Credentials

Observer Cloud is a dumping ground for credentials stolen during major data breaches. While the group does not conduct the breaches itself, it aggregates data from other sources and makes it widely accessible, often without requiring payment.
This makes the channel harmful if you are a common user, as leaked data from platforms like LinkedIn, Dropbox, or government records might appear here.
Caution: Many phishing scams and credential stuffing attacks stem from data first seen in this channel.
- Omega Cloud – Real-Time Malware Log Marketplace
Omega Cloud is a dark web-style marketplace operating on Telegram that specializes in distributing logs extracted from infostealers like RedLine, Raccoon, and Vidar. These logs often contain browser-saved passwords, session cookies, and autofill data.
The channel provides real-time updates on available datasets, so that victims can not even notice the breach.
Risk factor: Logs from this group enable attackers to bypass multi-factor authentication and hijack email, banking, and crypto accounts.
- Data Leak Monitoring
Although positioned as an alert service for recent breaches, the Data Leak Monitoring channel is also exploited by malicious actors to quickly monetize leaked data. Many of the posts include passwords, hashed credentials, and other identifying info scraped from exposed databases.
Verdict: Useful for awareness, but dangerous if used for malicious intent or credential harvesting.
- BidenCash CVV [ANTIPUBLIC] – Stolen Credit Card Marketplace

This Telegram channel is a black-market outlet for stolen credit card data, including CVV numbers, expiration dates, and issuing bank details. Some card dumps are provided publicly, while premium lists are sold to high-tier members.
BidenCash CVV is notorious for leaking data from international cardholders and is a frequent contributor to fraudulent online purchases and identity theft.
Red flag: If your financial information was compromised in a retail breach, it could easily end up here.
- EMP/mailpass/sqli Chat – Breach Forum and SQL Injection Hub

It operates as a hybrid between a hacking forum and a dark marketplace. It regularly shares:
- Mailpass combos (email-password lists)
- SQL injection dumps from compromised websites
- Marketplace links for access to deeper dark web forums
Users also exchange malware deployment tips, including phishing kit distributions.
Warning: Engaging with this group may violate cybercrime laws in multiple jurisdictions.
- Dark Storm Team – Hack-for-Hire Collective

Dark Storm Team is known for offering hack-for-hire services. The group operates globally and has been linked to politically motivated cyberattacks, ransomware deployments, and targeted doxing.
Their Telegram channel acts as a storefront for services including:
- DDoS attacks
- Social media hijacking
- Custom malware creation
Threat level: Very High. Even viewing some of the sample links or tools may expose your IP and device.
- Z-Pentest Alliance – Industrial Control System (ICS) Threat Group
Z-Pentest Alliance targets industrial control systems (ICS), SCADA networks, and critical infrastructure. This makes them a major national security concern, especially for utilities, healthcare, and manufacturing sectors. Their posts range from ICS vulnerability guides to leaked access credentials of supervisory systems.
Why it matters: Attacks coordinated by this group can lead to catastrophic outages, supply chain disruptions, and environmental hazards.
Discover if Your Most Critical Identifiers Have Been Exposed on the Dark Web
Receive timely alerts and actionable insights with PurePrivacy's Dark Web Monitoring.
Is Telegram a Safe Platform?
Telegram’s reputation as a secure messaging platform is under fire. While the app provides end-to-end encryption in “Secret Chats,” standard groups and channels are not encrypted. This exposes you to surveillance and data leakage if exploited.
Major Privacy Concerns:
- Unmoderated groups often host illegal activities such as CSAM, fraud, and drug sales.
- Law enforcement agencies in France, Germany, and Belgium have criticized Telegram’s non-cooperation.
- CEO Pavel Durov’s arrest over complicity in criminal activity has intensified scrutiny of the platform.
Despite Telegram banning many malicious groups, it has left many users, including us, vulnerable for too long.
If Telegram continues to resist cooperation with authorities, people will see it as a place for criminals, not a safe place for privacy and free speech.
Are There Any Safe Telegram Dark Web Platforms?
There are Telegram channels that share information about cybersecurity threats and data breaches. These channels can be useful for information gathering and staying informed, but you must remember that these channels could also have members whose motive is to gather and exploit your data.
7 Dark Web Chat Groups and Channels Considered Safe
- vx-underground
Well-known on Twitter, vx underground offers a collection of malware samples, research papers, and cybersecurity insights as a valuable educational platform for security researchers and enthusiasts. The platform promotes community awareness about data breaches and recent cyber threats.
- KelvinSecurity
This channel focuses on ethical hacking, sharing information about vulnerabilities, code reviews, and hacking tips. It acts as a guide for ethical hackers.
- Breached Data
Breached Data provides updates on sensitive data leaks, including security pins, phone numbers, and passwords. Works to raise awareness about global data breaches.
- The Hidden Wiki .onion v3
It is a directory of links to popular onion sites on the Tor network, offering a resource for finding onion links to various dark web websites.
- Best Free Courses
It provides resource material for educational purposes and has many subscribers.
- Dark Hidden Wiki
It is a directory of onion links for the Tor browser and provides a source for authentic dark web links.
7 Telegram Channels on the Dark Web (Educational & Informational Use Only)
| Channel/Group | Purpose | Pros | Cons |
| vx-underground | Cybersecurity research and malware analysis | Trusted by researchers for malware samples and real-world threat intel. Shares research papers and breach disclosures | Contains malware links, not safe for general users Could attract malicious actors |
| KelvinSecurity | Ethical hacking and vulnerability research | Promotes awareness of global CVEs Ideal for penetration testers and ethical hackers | May border on gray-hat practices Content can be misunderstood or misused |
| Breached Data | Updates on leaked databases and breach alerts | Raises awareness about global leaks Useful for companies to monitor brand exposure | Often shares real leaked data Can be misused for doxing or fraud |
| The Hidden Wiki .onion v3 | Tor directory links for dark web exploration | Curated list of active .onion links Helps researchers locate surface-dark web intersections | May include illegal sites Risky for casual users without proper protection (VPN + Tor) |
| Best Free Courses | Shares free learning resources in cybersecurity and privacy | Beginner-friendly Offers educational PDFs, eBooks, and video courses | Some links may lead to pirated or questionable material |
| Dark Hidden Wiki | Directory for Tor browser users | Useful for learning about .onion structure Helps in exploring dark web resources securely | Like other wikis, may contain unvetted or harmful links |
| DarkWeb News | News updates on dark web activity and threat actors | Real-time alerts on ransomware, carding ops, and takedowns Keeps you informed of law enforcement activity | May include unverified or sensational content |
Could My Data Be on Telegram’s Dark Web Channels?
Yes, even if you haven’t directly joined any dark web forums. If your data has ever been leaked in a breach (e.g., email/password dump), it may have been sold or shared on Telegram.
Risks Include:
- Phishing links or malware shared in groups
- Credentials harvested from past breaches
- Identity theft from openly posted documents
Is My Data on the Dark Web If I Am Using Telegram?
Not necessarily! Telegram's encryption, large group capacities, and anonymity make it attractive to cybercriminals, and these features facilitate the exchange of stolen data, hacking tools, and other illicit activities. Because of this, there are chances that if your data was a part of a data breach, it could end up being sold or shared on Telegram channels.
Also, Telegram is used for scams and malware distribution, which can lead to your data being stolen. Plus, malicious actors may use Telegram for phishing attempts or distribute malware that steals data.
Can I Prevent My Data from Ending Up On the Dark Web?
Data is the new gold! Whether you have accessed the dark web or not, you are prone to exploitation such as data leaks, tracking, unwanted ads, and blackmailing.
Plus, when organizations with your data are compromised, your sensitive details can end up on the dark web, resulting in multiple exploitations.
PureVPN’s Dark Web Monitoring tracks the critical identifiers that might have ended up on the dark web so you can take the necessary precautions before your sensitive data is misused.
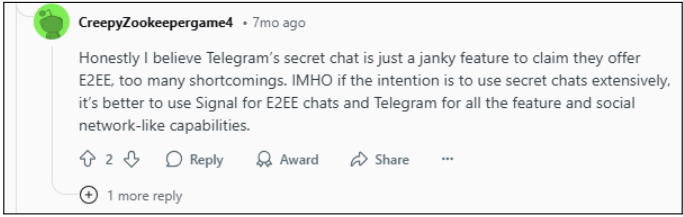
How to Enable Dark Web Monitoring on PureVPN
- Install PureVPN on your device or update your existing app.
- Visit the Members Area to get access.
- Go to Dark Web Monitoring from the main menu.
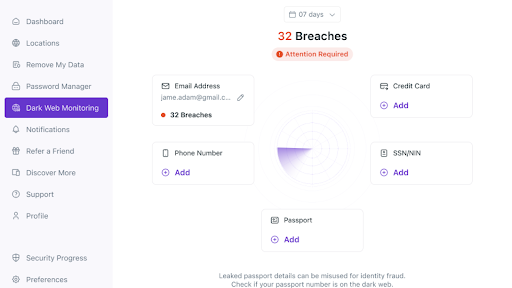
- Select Add Assets to Monitor.
- Add your email address, phone number, passport number, credit card number, and SSN/NIN.
- Mention the code sent to your registered number, and you’re done.
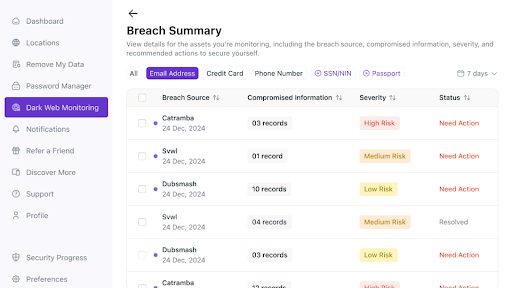
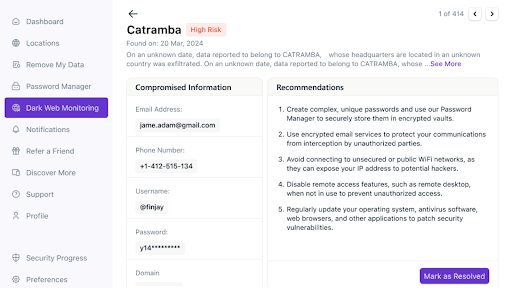
7. Take the recommended steps if your data is part of a breach.
8. You can also mark breaches as resolved.
Frequently Asked Questions (FAQs)
-
Can I access Telegram from anywhere?

You can not access Telegram in some countries where it has been banned due to government censorship and legal regulations. If you want to access Telegram, then you can use PureVPN and bypass regional barriers without getting banned.
-
How good is Telegram's privacy?

Telegram offers different levels of privacy. Secret Chats use end-to-end encryption, although the standard group chats and channels are not end-to-end encrypted, and Telegram technically has access to that data. Also, Telegram collects specific user data. You must read and understand the privacy policy before using any platform.
-
Can I join the Telegram dark web groups?

Yes, you can, but you must stay extremely cautious. Although some groups are made for education and community awareness, some malicious actors are working diligently to gather your data, which might later be used for malicious intent.
-
Is my data secure on the dark web?

No. The dark web carries greater risks. If your data is leaked once, you are vulnerable to hacking, malware, and identity theft. You must monitor your data with PureVPN’s Dark Web Monitoring to prevent future damage.
-
Can Telegram data be leaked?

Yes. All online platforms can leak your data due to poor security measures, data breaches, hacking, internal vulnerabilities, or other factors.
Wrap Up
Accessing the internet with complete freedom is all that we want. But if freedom comes at the cost of data being compromised, then it is too expensive. Telegram or any other communication network can be of great benefit to us, but remember, when it comes to accessing the dark web, you must stay vigilant.
Monitor, track, and manage your critical personal information with PureVPN Dark Web Monitoring!




