Table of Content
- Remove Your Data from Websites
- Delete Unused Apps
- Stop AI Training from Using Your Data
- Remove Online Public Records
- Restrict Personal Information Sharing on Smart Devices
- Remove Your History from Web Browser
- Remove Unused Social Media Accounts
- Remove Your Data from Data Brokers
- Delete Your Old Email Address
- Encrypt Your Hard Drive Data
- Remove Any Unused Web Extension
- 4 Things to Keep in Mind before Removing Your Information from the Internet
- Frequently Asked Questions (FAQs)
Data breaches happen every day!
Malicious actors are constantly searching for weaknesses to exploit.
Wouldn't it be empowering to take control of your online footprint and minimize the risk?
This blog explores practical strategies for managing your privacy.
We'll discuss how to remove my personal data from the internet from search results and how to request the deletion of data from particular platforms.
Remove Your Data from Websites
Your personal information won't disappear from the internet even if you remove it from Google. If you want to prevent anyone from discovering them, you must ask for the removal of your personal data and photographs from the website hosting them.
If not, the data will still be shareable on social media and searchable through other search engines.
Delete Unused Apps
Though phones might become overloaded with apps we hardly use, they are also great sources of information and entertainment.
In addition to taking up storage space, unused apps may reduce battery life and lead to security flaws, so it’s better to delete them to improve your security.
Delete Unused Apps on iOS Devices
An average iPhone user has 49 downloaded apps, but they only use 9 of them daily.
This emphasizes how uninstalled apps could pose a security concern. Ignoring permission requests from applications introduces problems because many of them ask to access contacts, locations, and even photos.
With Apple's "Offload Unused Apps" option, you can delete an app or multiple unused apps and save its login data for future reinstallation.
Delete Unused Apps on Android Devices
Unused apps can either use all mobile data or carry on gathering information about the phone and its owner and selling it to advertising companies.
One of the main issues brought on by digital data overload is an increase in invasive and uninvited advertisements that frequently exploit device weaknesses; poll participants noted this as an issue with smartphones 61% of the time.
Make sure your data is erased by checking the privacy and account settings before deleting any unused apps. In some cases, removing your personal data may require you to get in touch with the developer directly.
Stop AI Training from Using Your Data
The huge amount of data that we produce while using the internet powers the creation of strong AI systems. Despite all of AI's advantages, there are issues with the way our data is used to train these systems.
The monthly average of insider-driven data exposure, loss, leak, and theft occurrences has increased by 28% since 2021.
Although total control may be impossible, there are actions you can take to reduce the amount of data you generate and restrict its use for AI training.
Here are some most commonly used AI training models on which you can manage your online data prevention this way:
Gemini
Within Gemini's activity settings, you can choose to prevent their discussions from being used for AI training.
ChatGPT
Depending on the platform and account type, OpenAI offers controls that let you manage how their data is used for AI training.
Adobe
Through Adobe's privacy settings, you can prevent data from being used for AI training. However, to opt out, owners of corporate and educational accounts must contact administrators.
HubSpot
Since there is no automated method, opting out requires sending a direct email to HubSpot.
Grammarly
Personal accounts do not have the option to opt out of data training; however, business accounts do.
Slack
Only at the organizational level is it possible to opt out of Slack's use of your data for AI enhancement.
Remove Online Public Records
One important step in securing your security and privacy online is to remove any publicly accessible records you may have made. Because so much of your personal information is easily accessible online, identity theft is less likely.
These records may include your address, phone number, and even your birthdate, which are potential gold mines for identity thieves. By minimizing this online impression, you can make it much more difficult for someone to pose as you and create financial or legal issues.
The number of data breaches in the United States in 2023 reached a record high, according to the ITRC Annual Data Breach Report. An increase of 72% points above the previous record-breaking amount of compromises made in 2021.
How to Remove Public Records
You can remove your public records online by following these steps:
- Use a variety of search engines, and people search websites to look for your name. Make a list of all the websites that have your information on them.
- Look for removal alternatives; the method for opting out may vary depending on the website. On the website, look for an "opt-out" or "privacy" section. They may ask you to send a request via email, or they may have a web form.
- Send them opt-out requests, and adhere to the particular guidelines provided on each page.
- Removing something can take some time. The total removal of your information from all websites could take a few weeks or even months. You might have to check in again with a few sites.
Restrict Personal Information Sharing on Smart Devices
Many IoT devices are not made with security in mind, and manufacturers might not update them frequently. This makes them vulnerable to known flaws that hackers could take advantage of.
IoT devices have even been employed in massive botnet attacks, such as the 2016 Mirai botnet attack.
Potential attackers can connect directly to a lot of popular IoT devices—many of which are bought to enhance physical security—without the need for authentication or encryption because they are easily accessible through certain tools.
If you want to keep control over your data, you need to be vigilant about protecting your devices against potential privacy breaches and illegal access.
Here’s how you can ensure your devices’ safety:
Network Security
The network your smart gadgets are connected to determines their security. To prevent unwanted access, make sure your WiFi network is secured with a strong password and the most recent encryption standard, WPA3.
Configuring Privacy Settings
Spend some time going over and adjusting your smart gadgets' privacy settings. Restrict the amount of personal information you give the manufacturer, and turn off any functions that aren't required for the device to function.
Real-Time Recording
Voice assistants, such as Google Assistant, Alexa, and Siri, pay attention to your commands and orders. They record the discussion both immediately after and before the activation, even though they are only meant to function after the prompts are heard.
In the event of a breach, hackers or other outside parties may be able to access these recordings since they are frequently kept on their distant servers.
Ransomware
Ransomware attacks encrypt your data and demand payment to unlock it. Downloading unprotected files or clicking on malicious links might both result in this. Use reputable antivirus software with anti-phishing tools to keep yourself safe.
Remove Your History from Web Browser
Google uses your past searches to deliver a more customized experience. However, if you don't disable Web & App Activity tracking, this data, including voice and audio recordings, might be shared with other services.
To prevent Google from tracking your behavior, turn off Web & App behavior tracking.
The Norwegian Consumer Council released a new report called Out of Control: How the Online Advertising Industry Exploits Consumers. The report examines the dark aspects of the data economy and makes some surprising discoveries.
Remove Photos from Google Maps
Step 1: Log into your Google account on any browser and open Google Maps.
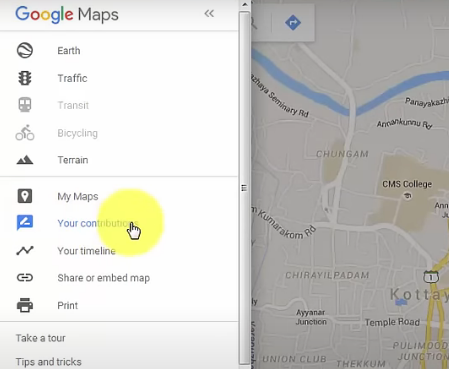
Step 2: Click the menu symbol (three horizontal lines) located in the upper-left corner of the Google Maps interface. Select "Your contributions" from the menu.
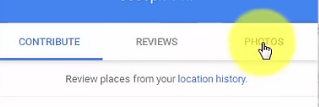
Step 3: Select the "Photos" tab from the "Your Contributions" page. This is a compilation of all the images you have added to Google Maps, arranged based on location.
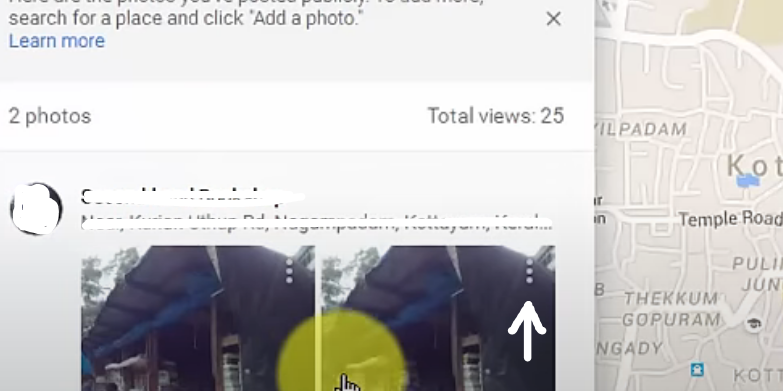
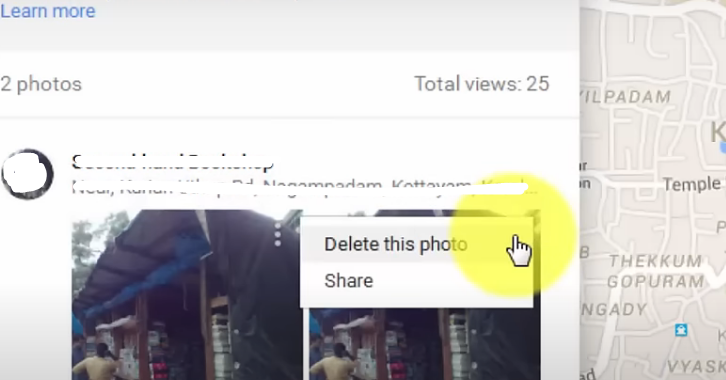
Step 4: Scroll through your photo contributions and select the photo you wish to remove. Click on the image to open it and see more details.
Step 5: The photo details page has three vertical dots in the top-right corner. When you click on these dots, a dropdown menu with different options will appear.
Step 6: Select "Delete photo" from the menu.
Turn Off Location Tracking
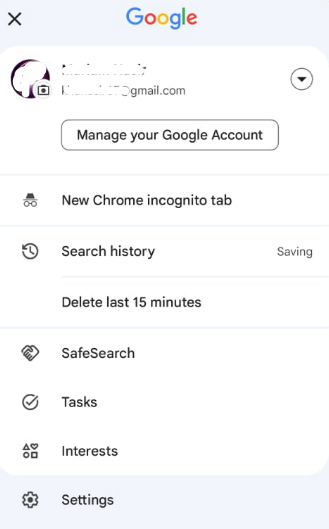
Step 1: Navigate to “Manage Your Google Account” after opening your Google account.
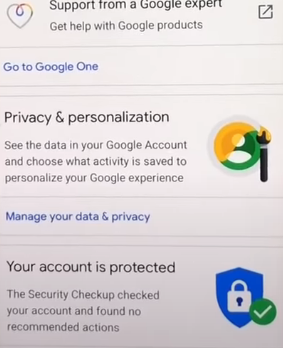
Step 2: Now, scroll down and click on “Manage your data and privacy.”
Step 3: Find and tap the “Location history”.
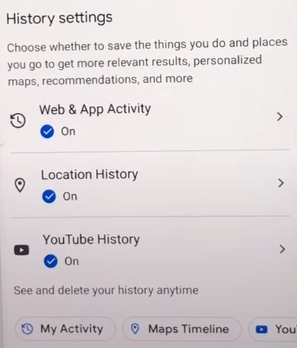
Step 3: You will see a “Turn off” button under location history, click on it.
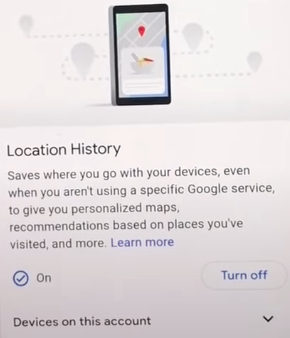
Step 4: You will head to a new page showing pause location history. Scroll down the page and click on the Pause button.
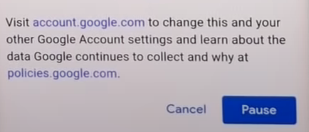
Turn Off YouTube Search History
Step 1: Open the YouTube app on your device.
Step 2: Click on your profile icon in the upper right corner of your screen.
Step 3: Click on “Settings.”
Step 4: Now, click on “Manage all history.”
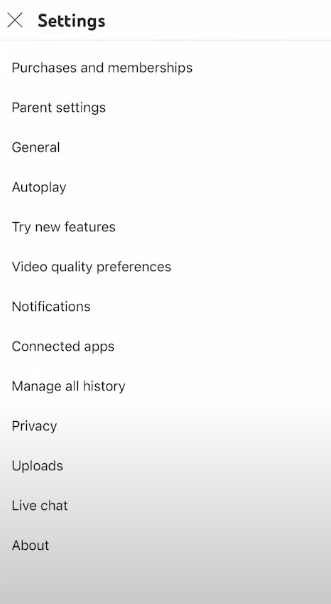
Step 5: To completely turn off your history, click on “Saving your YouTube history.”
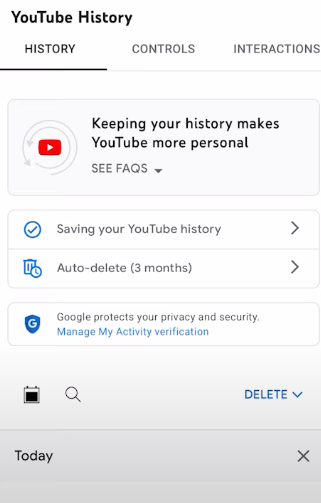
Step 6: Click on “Turn off.”
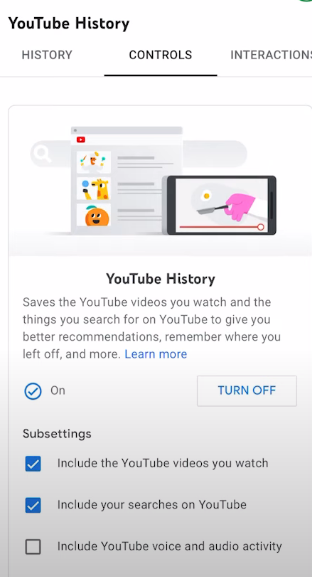
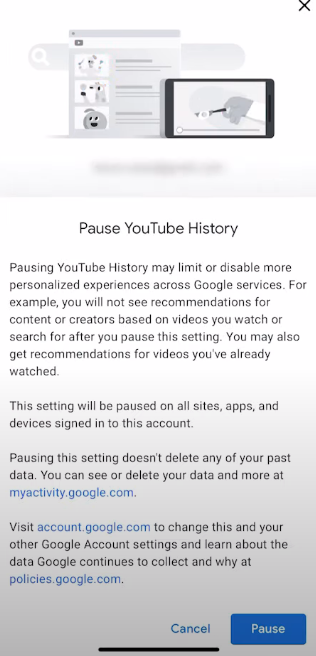
Step 7: Click on the “Pause” button to completely turn off your YouTube search history taking.
How to Delete Information from Yahoo
Step 1: Go to search.yahoo.com/history. Another option is to conduct a Yahoo! search and choose "Search History" by hovering over the Gear icon in the top-right corner.
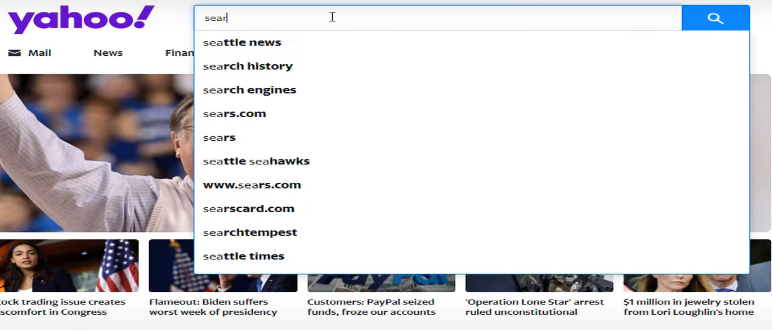
Step 2: Click on "Search History" from the left panel.
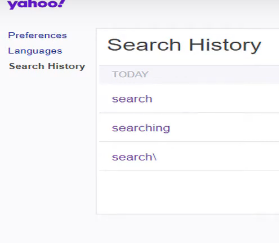
Step 3: Click the trash can icon to remove an individual entry. This button appears to the right of the entry in every search you have done.
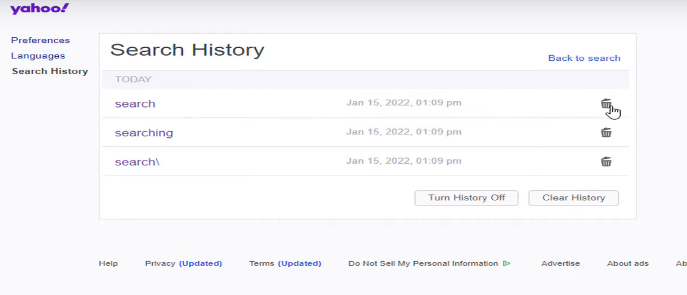
Step 4: Clicking the "Clear History" option will remove your search history.
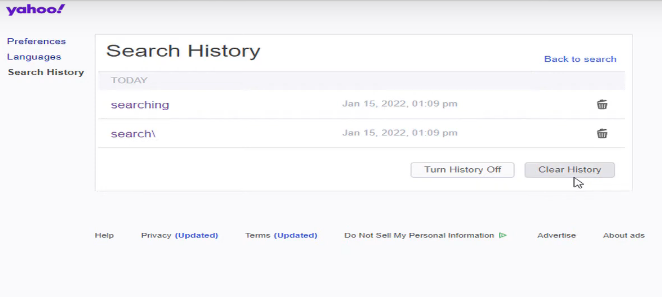
Step 5: Select "Turn History Off" to stop tracking going forward. Yahoo! will stop keeping track of your past searches.
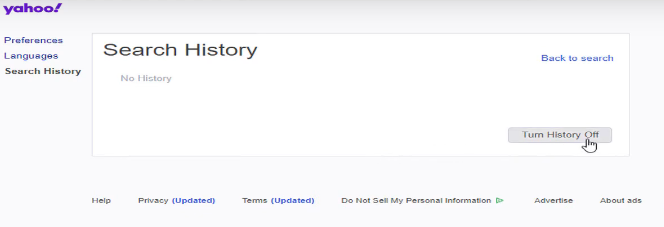
How to Delete Information from Bing
Step 1: Open up Bing in your preferred web browser.
Step 2: Select the gear symbol located in the upper right corner of the page, which signifies the settings. You'll see a drop-down menu appear.
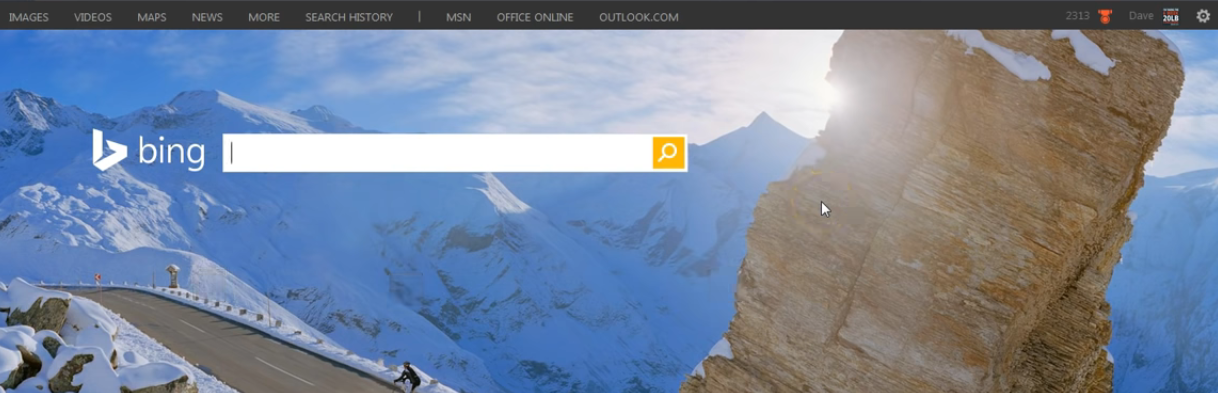
Step 3: Choose the option labeled "History" from the menu.

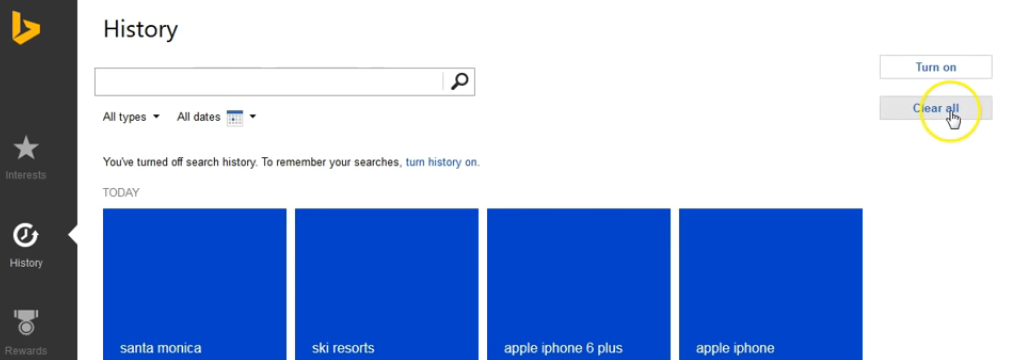
Step 4: Click the down arrow next to "Change History Settings" on the Search History page. If you don’t find the arrow, you can search the history by using the search bar or selecting date and type.
Step 5: Click the Clear All button that appears under the Change History setting.
Remove Unused Social Media Accounts
Long-term web surfers may have forgotten about old blog entries, personal websites, and other stuff (such as an inactive email account, Tumblr page, or social network profile) that is part of their online history.
Your personal information may be exposed by this content, and hackers may use it as a prime target to take over your previous accounts and deceive your friends and relatives.
According to a study, knowing that embarrassing photos or features from your personal information have been leaked online due to phishing schemes or inadequate security measures also causes a real mental health risk.
If you're not ready to give up your social media accounts, you should enhance your privacy settings by considering PurePrivacy.
It scans your social media accounts (Facebook, Twitter, Instagram, etc.) to find areas where your privacy settings could be improved. It also provides recommendations for customizing your security levels.
How to Make Your Social Media Accounts Private
The other way to protect your social media privacy is to make them private.
To make your Facebook account private, follow these steps:
Step 1: Follow these steps to make your Facebook profile private.
Step 2: Open Facebook on your desktop computer, iOS, or Android smartphone.
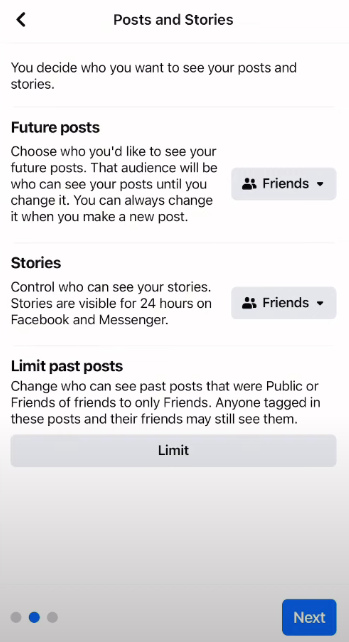
Step 3: Navigate to Settings & Privacy > Settings > Privacy Checkup after opening the Account Settings.
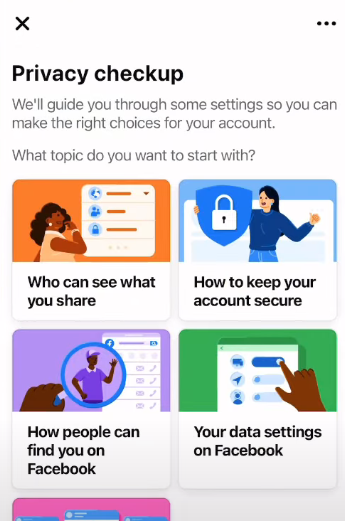
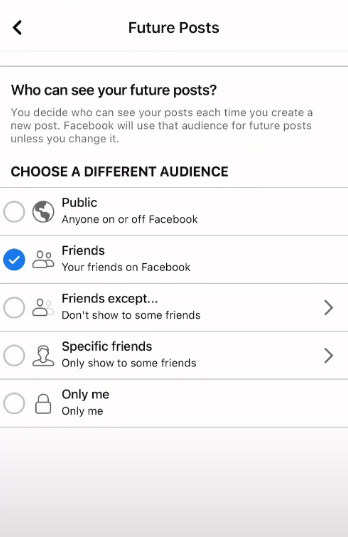
Step 4: Navigate to Who can view your future posts after Continue. To ensure complete privacy, select Friends or Only Me.
Use the instructions below to make your Instagram account private.
Step 1: Open Instagram, then go to your profile.
Step 2: To access the Menu, select the three horizontal lines located in the top-right corner of the screen.
Step 3: Choose Settings and Privacy.
Step 4: Pick Account Privacy from the Settings menu.
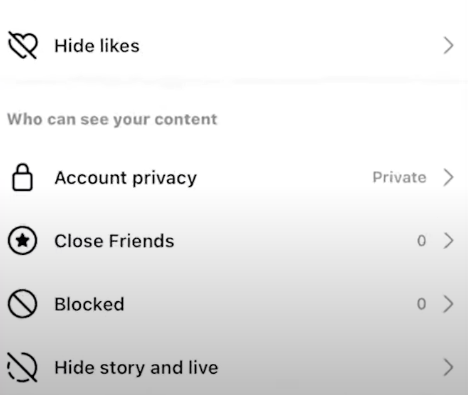
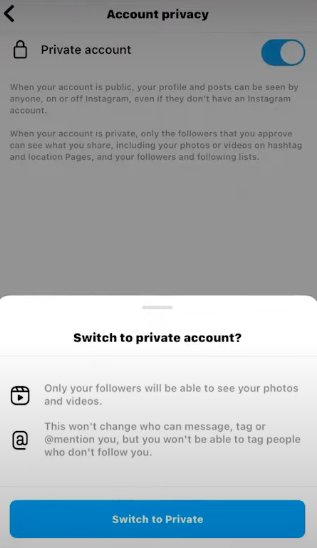
Step 5: Turn on the "Private Account" switch under Account privacy.
To change your Twitter account type from public to private, simply follow the instructions below.
Step 1: Open your Twitter account on your preferred device.
Step 2: A profile icon is in the upper left corner of the screen; tap on it.
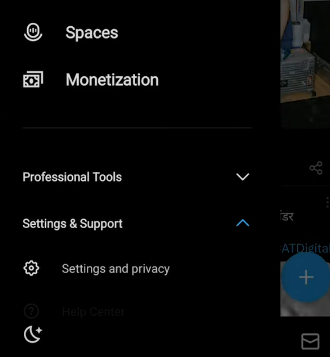
Step 3: Navigate to Audience and tagging under Settings & Privacy > Privacy and Safety.
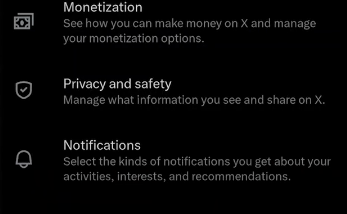
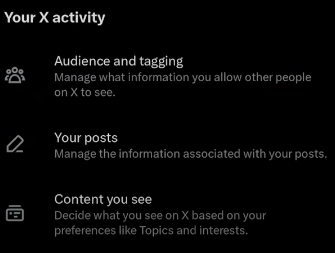
Step 4: Click on the "Protect your Posts" option. To confirm, choose Protect from the pop-up box.
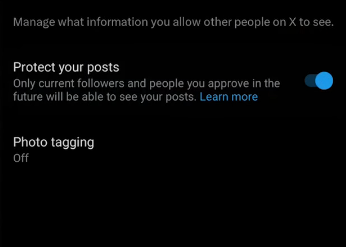
Snapchat
To change your Snapchat privacy settings, follow the steps below.
Step 1: After opening the app, go to your Snapchat profile page. To access your account settings, use the gear icon at the top-right corner of the screen.

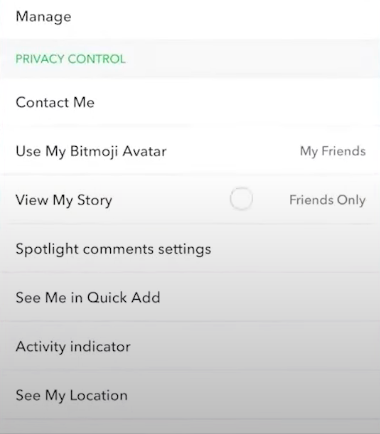
Step 2: Scroll down until you see the Contact Me option. Once you find it, click on it.
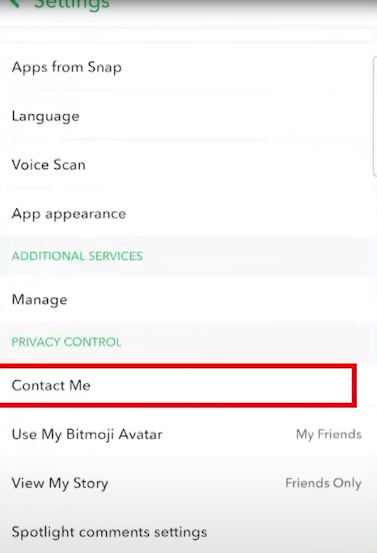
Step 3: Instead of selecting Friends and Contacts, choose Manage Who Can Contact Me and select Friends.
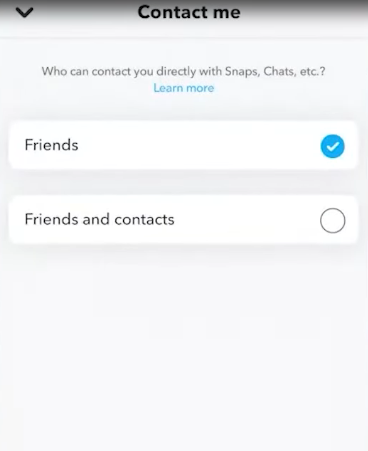
Step 4: Then, if you want to choose just who is permitted to view your Snapchat Stories, go back, click Manage Who Can View My Story, and change it to Friends Only or Custom.
Remove Your Data from Data Brokers
Data brokers, such as Innovis, People Finder, or CheckPeople, scan the Internet for personal data about you and build profiles they sell to advertisers or others.
Unfortunately, there are hundreds of data broker services in the US alone, and it can be complicated and time-consuming to try to get your data removed from each one.
Use the Privacy Rights data broker list to find all data brokers in your state or those with an opt-out procedure. PurePrivacy is one solution that removes your data from widespread broker websites.
To ensure that no one else, including marketers and scammers, receives your information, it requests data removal on your behalf and disables web trackers.
How to Stay Private on Multiple Browsers
Google Chrome
To "block third-party cookies," open the Chrome settings menu and navigate to settings > privacy and security > third-party cookies.
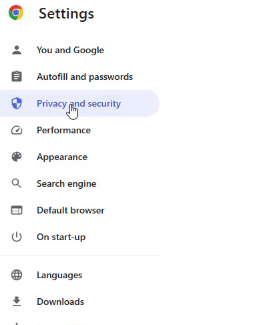
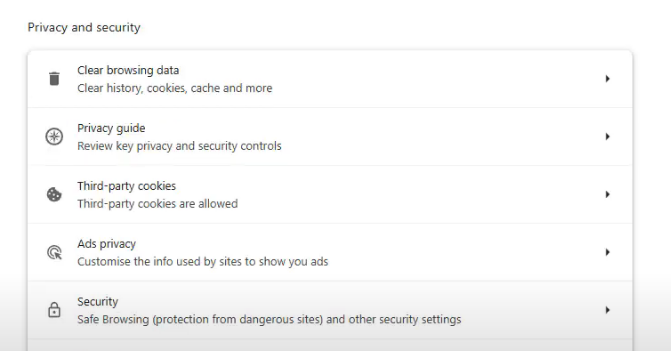
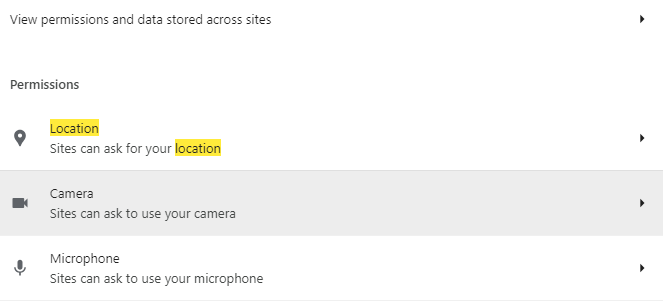
Return to privacy and security, then choose Settings > Site Settings from the menu. You can decide whether you want websites to be able to request your location or not.
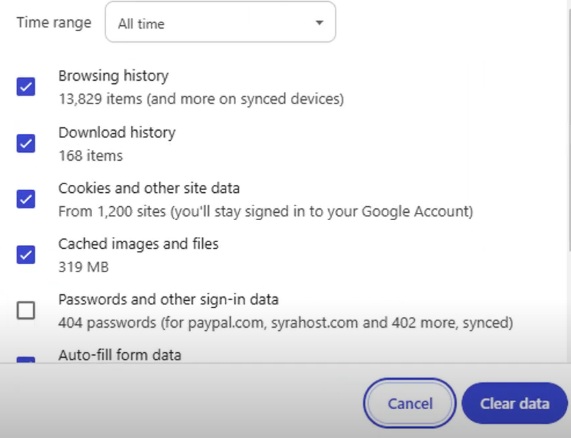
Return to privacy and security, choose "clear browsing data," make sure every piece of information you wish to erase is checked, and then press "clear data."
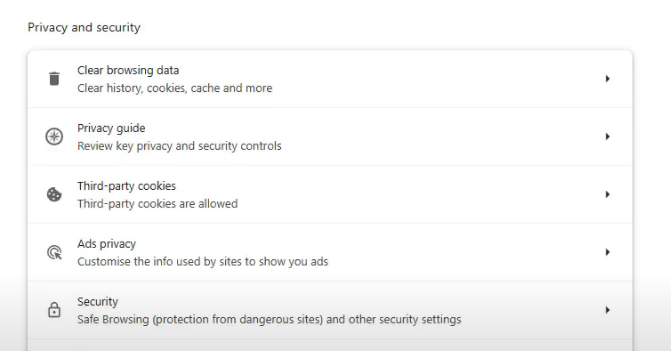
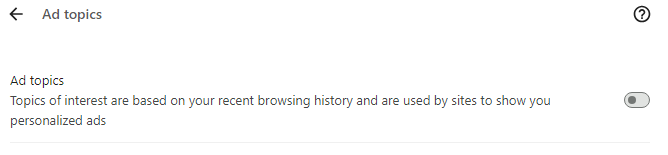
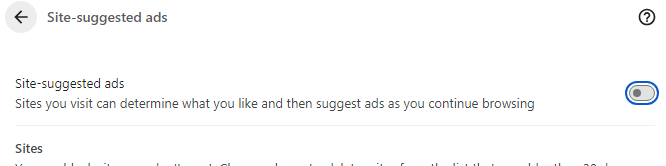
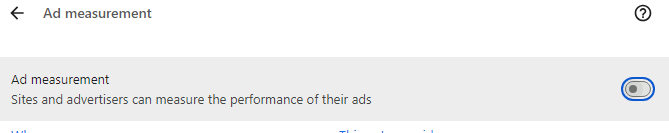
Finally, return to privacy and security, choose advertising privacy, and then toggle off the Ads measurement, Site-suggested ad, and Ad topics tabs.
Microsoft Edge
To remove cookies or other browsing data that have been saved on Microsoft Edge, follow these steps:
Step 1: Click on the three-dots icon and choose Settings > Privacy, search, and services in Microsoft Edge.
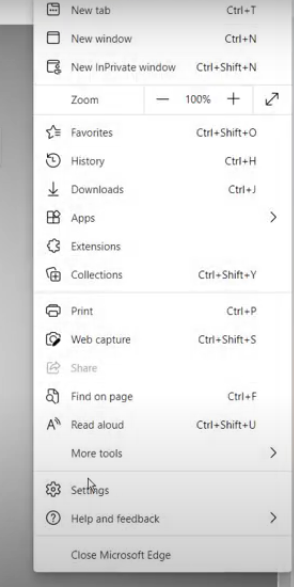
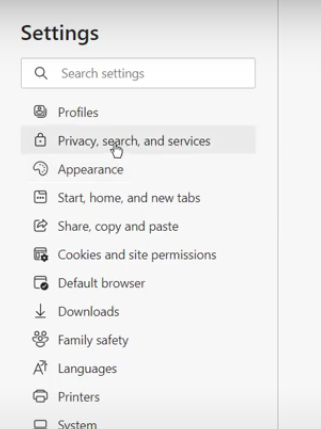
Step 2: Select "Choose what to clear" under "Clear browsing data."
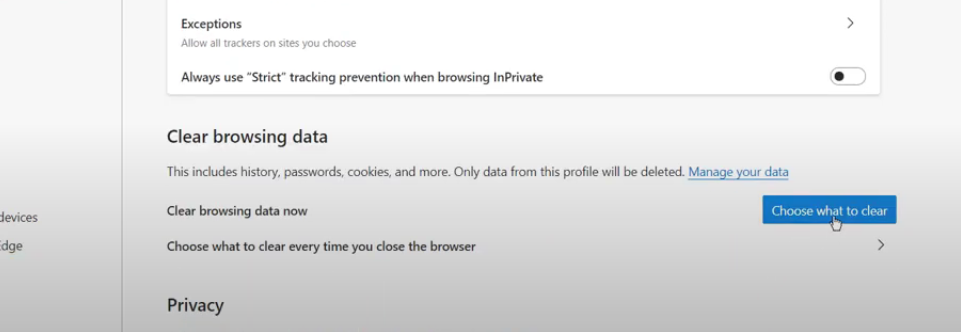
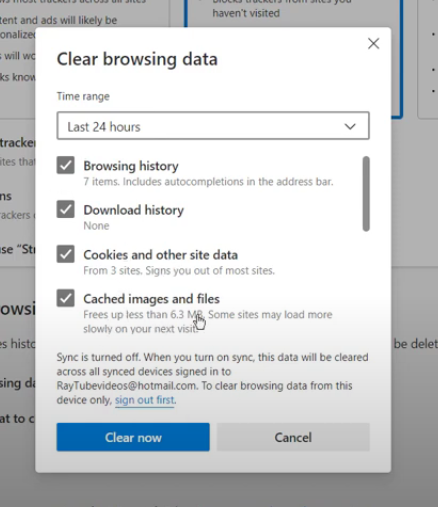
Step 3: Select a time range under Time range.
Step 4: To remove a particular sort of data, tick the box next to it, then choose Clear Now.
Opera
To remove your information and browsing data from Opera, follow these steps:
Step 1: Click on the three-dots menu icon and then click on the Browsing Data from the menu.
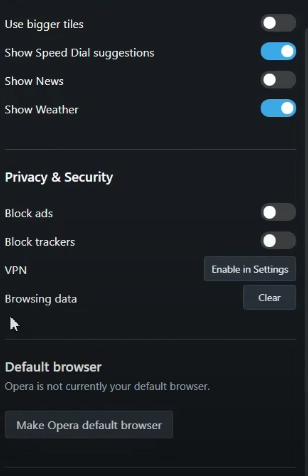
Step 2: Click on Clear Browsing Data.
Step 3: Make sure Cookies and other site data as well as Cached images and files are chosen, then pick All Time from the time range dropdown. Click Clear Data after making your selections.
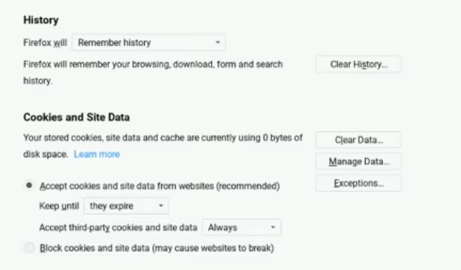
Firefox
To remove cookies or other browsing data that have been saved on Firefox, follow these steps:
Step 1: Press the menu button.
Step 2: Select Preferences.
Step 3: To access privacy and security, scroll down.
Step 4: Click Browsing History.
Step 5: Next to the things you wish to clear, make a mark.
Step 6: Select "Clear browsing data" by tapping it.
Step 7: Tap Clear Data in front of Cookies and Site Data.
Delete Your Old Email Address
This statement only applies if you have old email addresses. Still, this is a significant security consideration.
91% of all attacks reportedly start with a phishing email sent to an unaware victim. Furthermore, phishing scams are used in 32% of all successful data invasions.
Email addresses include personal data, confidential messages, purchase receipts, sensitive financial information, and medical records. As a result, an email account breach might have severe consequences.
Encrypt Your Hard Drive Data
Any device with sensitive data, such as an external hard drive or laptop that is not locked, is at risk of data leakage. Put a strong password on the drive and encrypt your data.
This blurs the data, making it unreadable even if someone manages to access the drive. Specific drives have built-in encryption, or you can encrypt the drive with software.
Most recently, Dell verified a data breach allegedly involving "49 million customer records." Dell has acknowledged the existence of a violation, but it has not yet been established to what extent.
According to reports, a hacker on the Dark Web claims that the 49 million records—containing data from 2017 to seven years ago—are part of the breach.
Remove Any Unused Web Extension
Removing outdated browser extensions shares similarities to organizing your bookmarks. However, most extensions pose a security and privacy risk because they have access to everything you do in your browser.
Occasionally, if your browser updates to offer that feature by default, extensions may no longer be necessary. In other cases, a significant browser update or a lack of maintenance could cause an extension to break.
Therefore, uninstall any old or malfunctioning extensions from your browser to get rid of linked data.
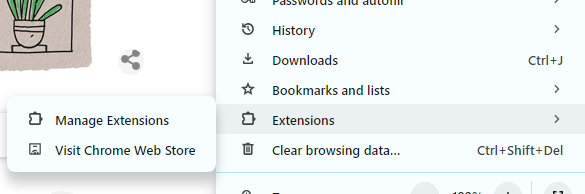
How to Remove Unused Chrome Extension
Here’s how you can remove any unwanted Chrome extension from your browser:
Step 1: Click the three dots in the upper right corner of Chrome after opening it.
Step 2: Click Manage Extensions after selecting Extensions.
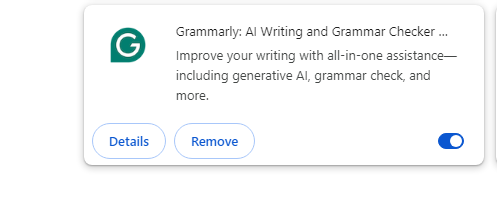
Step 3: To eliminate any Chrome extensions or apps that you no longer want, click Remove.
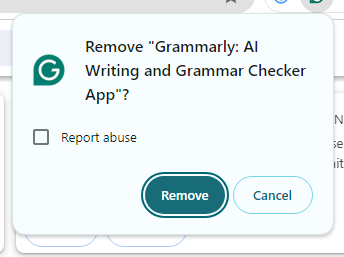
Step 4: Then click Remove again to be sure the removal was successful.
4 Things to Keep in Mind before Removing Your Information from the Internet
Before deleting your data from the internet, keep the following factors in mind:
Data Removal is a Continuous Process
Since the internet constantly evolves, more details about you might surface online. Be ready to repeat the removal process, and watch for fresh information.
Backup Your Data
Before deleting any accounts or information, ensure you have backups of all significant data, including messages and images.
Do Your Privacy Checkup
Do an internet search to find out what details are available to the general public.
Update Your Social Media Privacy Settings
Ensure that your social media accounts are private, allowing only those who have been permitted to view your information.
Enhancement in Data Privacy Policies by the Tech Industry
How the IT industry manages user data is coming under more and more criticism. Data privacy laws are being significantly developed in response.
Stronger Laws
Two prominent examples of stricter regulations are the California Consumer Privacy Act (CCPA) in the US and the General Data Protection Regulation (GDPR) in the EU. These regulations call for transparency in data collection, usage, and storage and give users more control over their data.
Global Impact
There is a growing standardization of disparate data privacy rules worldwide. This trend will likely continue, forcing businesses to adopt uniform data privacy policies everywhere.
Clear Communication
User-friendly data privacy rules are emerging, providing concise descriptions of the types of data gathered, how they are used, and who they are shared with.
User Control and Access
You now have more ability to see, download, and even remove your data. Businesses are developing systems to make these activities smoother with data policies.
Is it Possible to Get Your Personal Information Removed from the Dark Web?
The Dark Web is a hidden, limited portion of the internet that can only be accessed with specialist web browsers. Because it is nearly impossible to track down hackers on the Dark Web, it is perfect for illicit and anonymous communication.
Your personal information is vulnerable to being exposed on the Dark Web if a firm you do business with experiences a data breach.
Unfortunately, once your personal information is out there on the Dark Web, it's nearly hard to get it taken down.
If you want to make sure your data hasn't been compromised, you can utilize a Dark Web monitoring service.
How to Protect Your Online Privacy
These days, maintaining your privacy online is crucial, and there are several precautions you can take to keep yourself safe. Here are some crucial aspects to pay attention to:
- For each account you have, come up with a complex and unique password. You can generate and save secure passwords with the aid of a password manager.
- Whenever possible, turn on two-factor authentication (2FA). By requesting a second verification code in addition to your password upon login, this provides an additional degree of security.
- Check and adjust the privacy settings on your other online services, including social media accounts.
- Identify cookies and how websites use them. To prevent cookies, either delete them from your browser or change its settings.
These suggestions can help protect your online privacy and make information theft by hackers and scammers more difficult.
Alternatively, you can use a more secure and complete security solution service like PurePrivacy.
Frequently Asked Questions (FAQs)
-
How to remove information from Google?

You can remove information from its Google search by completing a removal request. Just go to Google's Request to Remove Personal Information form and select Remove information you see in Google Search.
-
What are the best tools to remove my information from the internet?

There are various tools available online that claim to remove your information for free or for a fee. The idea is to realize that not all software can be trusted with our private data. These deletion applications also keep logs on you and must be used with caution.
-
Is it possible to know how many times my name is Googled?

No, it is not possible to know how many people have searched for your name. Google does not disclose this information to you or anyone else.
-
Can I delete my data on the dark web?

Deleting your data might not be possible on the dark web but you can mitigate the risks you might experience. Follow the best privacy practices and keep control over your data.
Don’t Let Your Data Leak!
Remember that maintaining your online privacy is a continuous effort. Thus, it is necessary to review your accounts frequently and change the settings.
This is particularly crucial given the alarming results of the Pew Research Center's 2024 survey on privacy attitudes, which showed that 81% of the public is concerned about how businesses exploit their data.
You can get help removing your information from search results using tools like Google's "Results About You."
For a more comprehensive privacy strategy, consider trusted internet privacy services focusing on privacy management.