Cybercriminals are exploiting phone numbers as entry points for identity theft. From crossing security protocols to SIM swap attacks, the misuse of phone numbers is increasing. You must know how vulnerable your phone number is and must protect it to prevent identity theft and other cyber crimes.
3 Critical Roles of Phone Numbers in Identity Theft
Phone numbers have become attractive targets and valuable assets for identity thieves. Here’s what cybercriminals do with your phone number:
- Authentication and Account Recovery
Many online services use phone numbers for two-factor authentication (2FA), password recovery, and account verification. If a malicious actor gains control of your phone number, they can intercept verification codes or reset credentials, enjoying unauthorized access to sensitive accounts.
- Social Engineering Vector
With just a phone number, attackers can launch phishing campaigns, impersonate trusted organizations, or gather additional personal details through voice phishing. Phone numbers are often linked to publicly available information, which can be used for scams.
- SIM Swapping and Number Hijacking
SIM swapping can convince a mobile carrier to transfer a victim’s number to a SIM card controlled by the attacker. Once successful, the criminal can receive all calls and texts, bypass 2FA mechanisms, and reset access to financial accounts or social media platforms.
How to Safeguard Phone Number Information?
Identity thieves will always find ways to find your essential data and use it for malicious purposes. Here are some practical tips you must follow to keep your Phone Number info safe:
1. Be Selective About Sharing Your Number
Never share your number unless it is very important. Avoid filling out forms such as surveys or signing up for non-essential services. Also, read and understand the policies of companies that require your data.
2. Use a Secondary Phone Number
Try to get a virtual phone service (e.g., Google Voice, Burner, Hushed, or Sideline) if you really need to provide a phone number to any service.
3. Enable Security Features on Your Phone
Use device protection so that your number is safe if your phone is stolen. You can enable "Find My Phone" (iOS) or "Find My Device" (Android). Keep your phone's software and apps updated.
4. Manage Calls and Messages
Try not to answer unknown phone calls or respond to shaky messages. Instead, block unknown callers through a built-in feature on your phone or through apps.
5. Protect Your Accounts
You can also set a PIN or passcode on your mobile carrier account. Enable Two-Factor Authentication (2FA) whenever possible. Try to create strong, unique passwords for all your online accounts.
6. Be Cautious Online
Use privacy-focused browsers, and only download apps from official app stores (Google Play Store, Apple App Store). It is also important to review app permissions before installing any application.
7. Report Spam and Scams
Report spam messages to the authorities, such as phone carriers or, in extreme cases, law enforcement.
8. Remove Your Number from Public Listings
Remove your phone number from social media profiles and other search websites to reduce your vulnerability to spam callers.
9. Secure Your Voicemail
Keep a strong PIN for your voicemail to prevent unauthorized access, and also check for any suspicious activity.
How to Protect Your Phone Number from Being Used in Identity Theft?
Your PII, including phone number, SSN, credit card details, and more, can be shared and sold on the dark web, leading to multiple exploitations.
You must protect your data and keep track of where it is shared. Here’s what to do:
- Sign up for PureMax.
- Download and install the PureVPN app.
- Log in to your account and select Dark Web Monitoring.
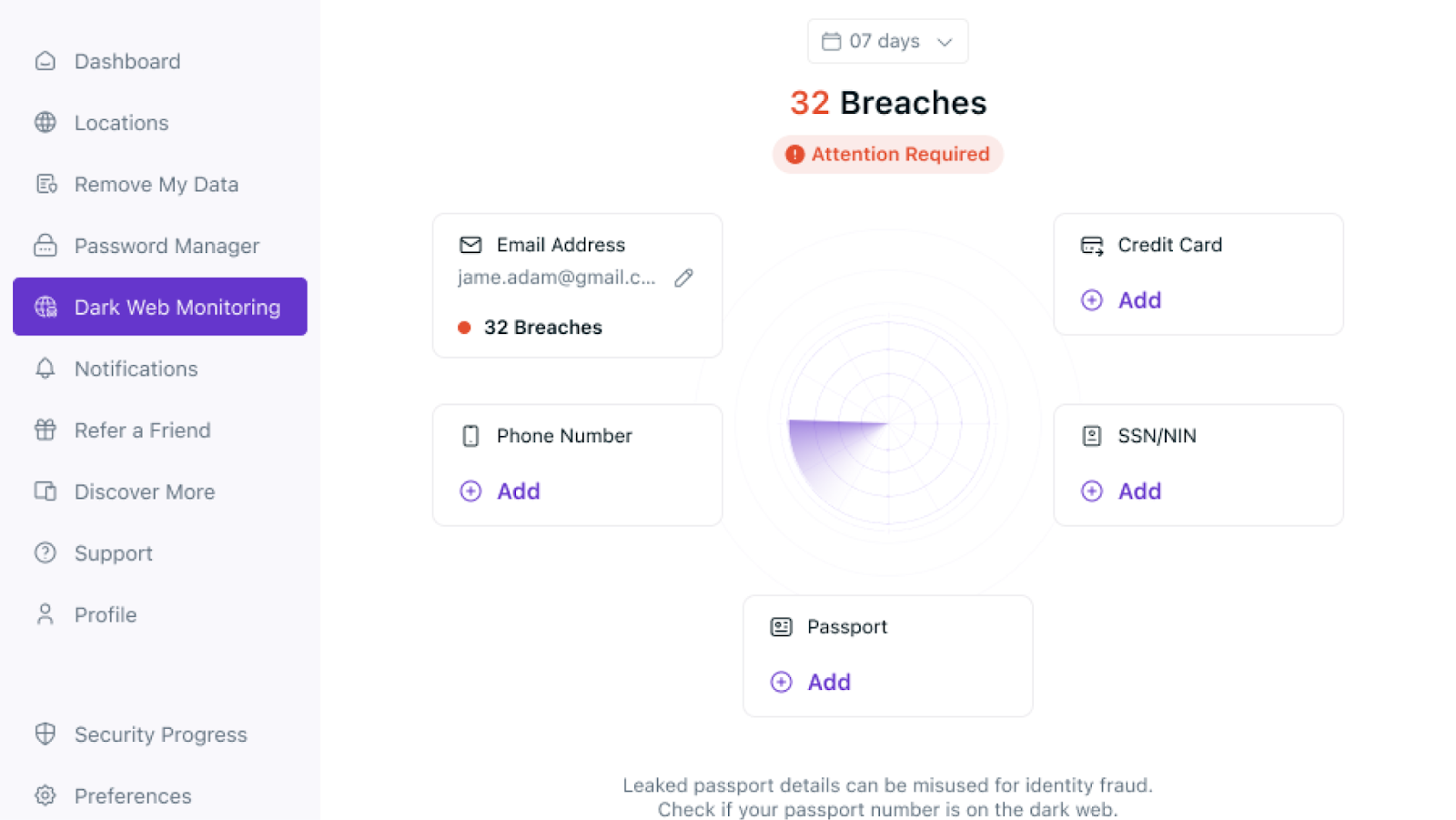
- Select Add Assets to Monitor and add your email address, SSN/NIN, credit card number, passport number, and phone number.
- Enter the code sent to your registered number, and you’re done.
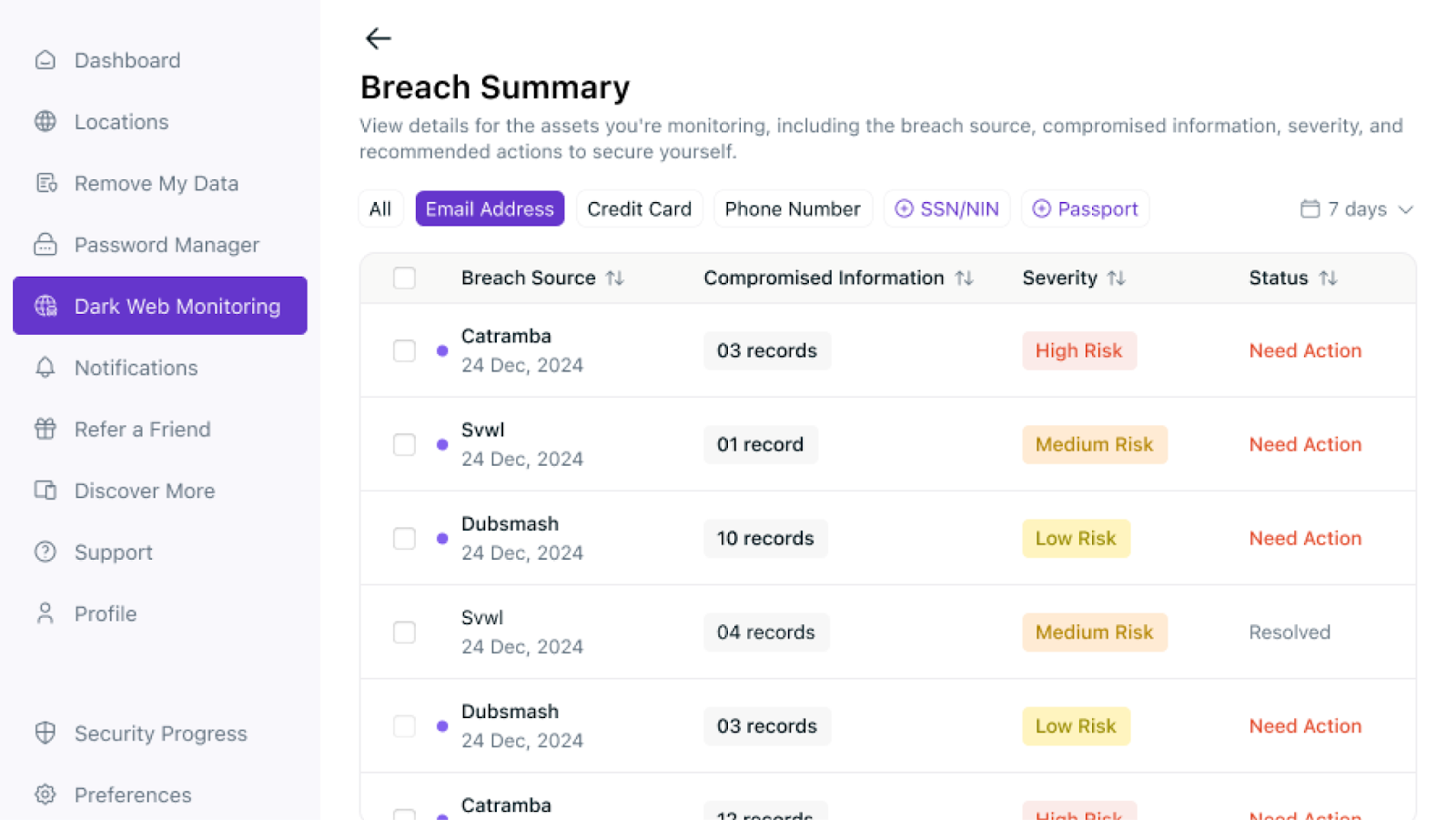
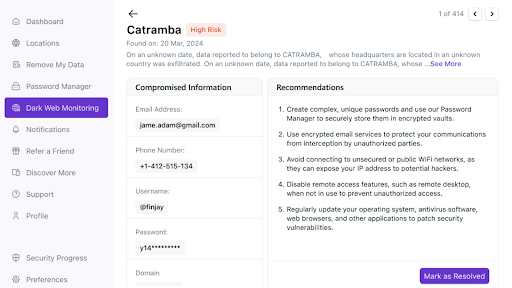
- Follow the recommended measures if your data is part of a breach to prevent further misuse.
Frequently Asked Questions
-
What if my Phone Number is on the dark web?

If your phone number is leaked on the dark web, it could be used for criminal activities that could lead to financial damages or could also damage your reputation. It could be used for spam calls and SMS messages, scams and phishing, SIM swapping, doxing, blackmailing, and more.
-
Is a phone number considered personal information?

Yes, a phone number is personal information because it can be used to identify or contact a specific person.
-
Can a scammer get into your phone with your phone number?

Directly accessing your physical phone with your phone number is unlikely. However, a scammer can use your phone number to compromise accounts linked to it or manipulate systems that trust it as an identifier.
-
What information can someone get from a phone number?

Your phone number can reveal basic personal details, location data, linked accounts, and some behavioral data.
Wrap Up
Protecting your data is no longer optional; it is essential. With PureVPN’s Dark Web Monitoring, you can proactively track, monitor, and protect your information. Stay informed about where your data is being shared without your consent and take action before threats escalate.



